The personal data of hundreds of Argentine customers of a series of household appliances and products has been publicly disclosed on the Internet, without any kind of password. The database belongs to Handel’s home page, whose stores sell products for the home in about thirty cities in the province of Buenos Aires. “Vulnerability” on the article series customer information for home It was discovered by American computer security consultant Jeremiah FowlerTogether with the research team planet locationwho submitted a report to which he agreed Infobae. Fowler is a manager Security Research from the side safety discoverybased in Europe.
From the company after consultation InfobaeThey downplayed the episode. “In response to the event consulted regarding a computer data breach, our company wishes to express its exposure to an attempt to hack one of our development servers in the said attempt They could not access the entire databasesBut only for a base of indicators that have less information than can be obtained from electoral rolls.” Gustavo SanchezHandel manager.
They explained from the company that it was a “development or test server, not the server used for sales,” and that they “were able to access the customer index but not the entire base.”
As a cyber investigator, Fowler often discovers “weak spots” in databases of personal information Online It belongs to companies or governments in different countries of the world. Infobae He asked him how he found Hendel’s exposed database on the web. “We use multiple scanning tools and iOT engines to identify misconfigured cloud storage networks. Once we expose this data, we validate our findings and try to understand what is exposed, who exposed it, and what the real world risks are,” Fowler replied via mail mail.
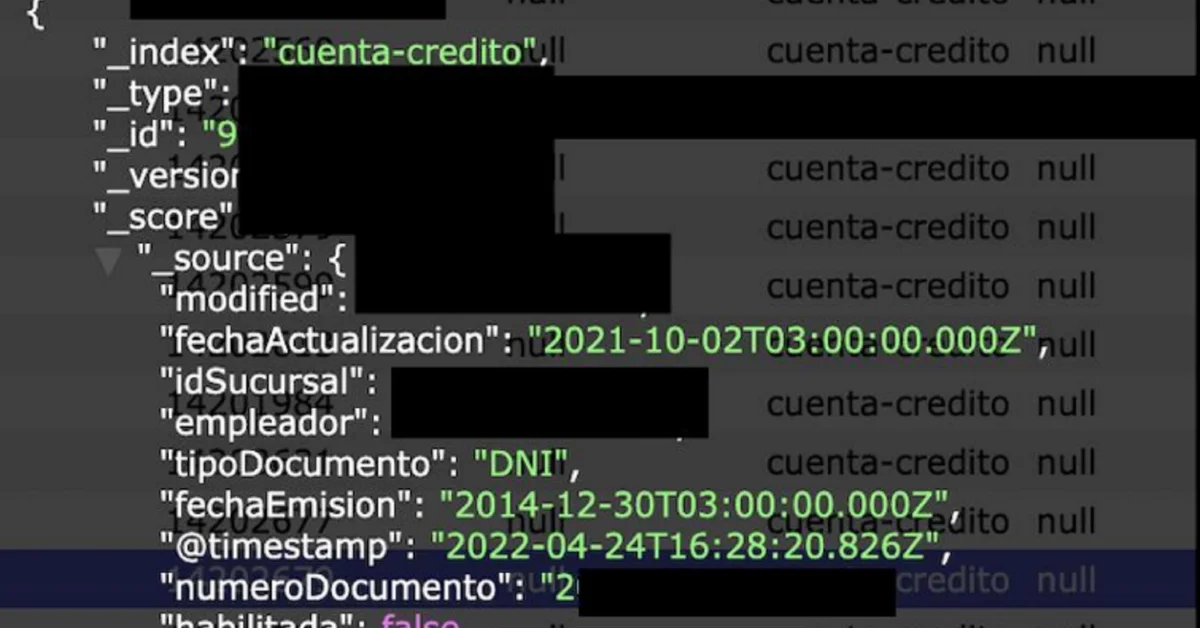
One of the leaked folders of this house called “Customer” contained 605,725 records with personal data of those who would be customers of Hendel stores.while another called ‘Credit account’, had 283,000 entries rIt refers to those who have resorted to credit to purchase items at Hendel Hogar. In total, they added 918,395 data. They explained from Hendel that they don’t have that many clients, and that “this number of registrations is much higher.” They also noted that “since it is a development server, it was intended to stress-test it to prove it, with some data from real clients and some false.”
Hendel Hogar is headquartered in Marcus Paz and has 31 branches, according to its website. Founded by Miguel Hendel, it sells everything from home appliances, computers, and home products to garden and camping tools, tools, sportswear, and toys. It also offers the possibility to take out your credit card. “For more than 50 years, our customers have trusted us to get access to those products they need, and we make this easier by giving them personal credit with their Hendel Card,” the chain promotes on its Facebook.
:quality(85)/cloudfront-us-east-1.images.arcpublishing.com/infobae/OKLC24XSDJEBRP4CSGN4N46FAU.jpg 992w)
Fowler alerted Hendel via email on May 24, with screenshots of what he had discovered. He said that although he did not receive any response Infobae That hardware chain shut down access to the public in less than three hours.
The company’s interpretation differs from Fowler’s. “This attempt was reported by Jeremiah Fowler via email, who warned us about the hack, and asked if the company had a bounty program for detecting computer vulnerabilities like the one reported. In the same notice, Fowler told us it had not implemented any kind of types of data mining, but only certain screenshots with the intent of notifying us of this and verifying its discovery,” Sanchez said. “At the date of receipt of the aforementioned email, the company’s experts confirmed that at that time there was no vulnerability,” Hendel’s manager confirmed. “Four days later, we received a new email from the same person stating that the vulnerability no longer exists, and we are again requesting the bounty program,” he added.
Beyond these versions found, It is not known if someone else can access the database while it is being exposed on the network. “There was a risk that it could be the target of a ransomware attack or be stolen by cybercriminals. If malicious hackers found the server, customers exposed to scams could be targeted through social engineering or identity theft tactics,” said Fowler, co-founder of Security Discovery.
As explained, an attack by ransomware andIt’s kind of Malware (or malware) that prevents users from accessing their system or personal files and requires a ransom payment to gain access to them again. “The ransomware It can infect your computer in several ways. One of the most common methods today is malicious spam, which is unsolicited messages that are used to send Malware By email. The email message may include false attachments, such as PDF files or Word documents. It may also contain links to malicious websites. Infobae.
Information displayed on the web
The Customer name and identification number are part of the exposed dataalthough the database does not contain complete scans or images of each individual’s document.
:quality(85)/cloudfront-us-east-1.images.arcpublishing.com/infobae/BRT7LH3WRNFUHFOQYEAHOWTS5M.png 420w,https://www.infobae.com/new-resizer/7_9ZaHwE7NFgc9otYUB-P1DidPk=/768x576/filters:format(webp):quality(85)/cloudfront-us-east-1.images.arcpublishing.com/infobae/BRT7LH3WRNFUHFOQYEAHOWTS5M.png 768w,https://www.infobae.com/new-resizer/0W99ECWW60drBO2QUkovXEVnVVM=/992x744/filters:format(webp):quality(85)/cloudfront-us-east-1.images.arcpublishing.com/infobae/BRT7LH3WRNFUHFOQYEAHOWTS5M.png 992w,https://www.infobae.com/new-resizer/reqRs4-8a-B3VOCCeKf7D3uW5L0=/1200x900/filters:format(webp):quality(85)/cloudfront-us-east-1.images.arcpublishing.com/infobae/BRT7LH3WRNFUHFOQYEAHOWTS5M.png 1200w,https://www.infobae.com/new-resizer/-7YYT-ZXZ7ZTJ1jo9ccwuqSTU38=/1440x1080/filters:format(webp):quality(85)/cloudfront-us-east-1.images.arcpublishing.com/infobae/BRT7LH3WRNFUHFOQYEAHOWTS5M.png 1440w)
Perhaps the most sensitive personal information contained in the exposed database is in each customer’s “credit account”. This identification appears to be a 6- or 8-digit internal tracking number for those who purchased items on credit, as Hendel offers its credit card as a payment option. “These numbers are arranged in chronological order from 000001 to 283,000, and are marked as enabled or active accounts,” Fowler said in his investigation. But when you ask Infobaehe explained that none of the records contained 16 digits, which is the usual number of digits on credit cards.
“This exposed data, such as name and identifier, can be used by computer or common criminals to commit fraud against these customers. Individuals can be identified using open source log search engines that show where they work and other data that can be used to create a complete victim profile and commit identity theft crimes,” this computer security researcher warned.
Files displayed publicly on the web also showed where the data was stored and how the “login” network worked.back end”. “When someone sees a store, business or service, they usually don’t know how to manage their customers or their credit accounts, and can only guess. In this case, we didn’t need to guess because anyone with an internet connection could see the architecture and clues of how the system would work or Given this data disclosure, we were able to learn what information was collected, how internal numbers were organized, and even how accounts/clients were stored in individual folders. end of introduction (interface) and back end (or an internal/development part). For example, is end of introduction It will be what customers see and not password protected, as CMS or database is an infrastructure for back end Fowler explained it Infobae.
:quality(85)/cloudfront-us-east-1.images.arcpublishing.com/infobae/EAXYPX3KUJEOLBCVWHLXX5WYUA.png 992w)
Hendel’s manager categorically denied any leakage of sensitive information. “We make it clear that our customers’ database and their confidential information is accessed by duly authorized company personnel according to their operational needs, and only through the company’s network, which is not directly exposed to the Internet.”
In accordance with Hendel’s privacy policy as responsible for the database of customers, human resources, suppliers and providers, the company has registered the databases with the National Directorate for the Protection of Personal Data, and implemented the updated renewals required by Law No. 25326 on the protection of personal data enacted in 2020. The rule for data protection was enacted Personal, allowing citizens to access information stored in public and private databases, in other records.
In the report prepared by Fowler approved it Infobae, except that disclosure of the data may not have caused harm to those whose data may have been exposed. “We are not suggesting that Hendel customers or credit applicants were at risk. We only highlight aspects of our discovery to raise awareness about data protection. We advise any company experiencing a data breach to conduct a criminal audit and notify affected customers or individuals to be vigilant about any changes to their credit accounts.
On the reasons for his dedication to revealing security flaws in online databases with individuals’ personal information, he explained: “We are a group of white hat hackers (or ethical hackers) focused on exposing these threats wherever we can. We find them. We do this by identifying flaws or loopholes in Corporate online security ourselves, then report it to the data owner, then share the results here on our blog to help others avoid making the same mistakes and internet users to protect themselves.”
“We believe that individuals deserve privacy and data security, no matter what country they live in or what language they speak,” he added.
Other massive leaks
This is not the first time that Argentina has experienced such a large-scale incident in recent years.
In 2020, the Argentine subsidiary of Telecom was hacked and its data was encrypted with an extension ransomware affect customer service systems. From Russia, they demanded a ransom of $7.5 million in cryptocurrency to return the files, but to no avail, as they could be contained. As they confirmed from the company, users were not affected The company’s call center was forced to suspend its service.
in the same year, The National Directorate of Migration was also a victim of assault before ransomware Under which the personal data of more than 25,000 Argentines who returned to the country amid a pandemic were leaked. More than 2,000 Internet users have downloaded files that are published on the platform of Ukrainian origin.
And last year, A hacker claimed to have the identification data of 45 million Argentines, extracted from RENAPER, although the agency denied the existence of heavy discharge. The hacker posted the private data of 44 Argentine public figures with a photo of their original ID on Twitter account.
Read on:



:quality(75)/cloudfront-us-east-1.images.arcpublishing.com/elcomercio/K3DAAUI4AVCF3GPFSRBCSPOLTA.jpg)
